PC as well as all other electronics need maintenance, maintenance and need the attention of the user during use. But many of us have some bugs to the "care" not good cause computer problems on hardware, software, worse, data loss. Previously we had pretty much all share about what to do, but what not to do something, why?
1. Do not update your operating system and your applications
I know that the updated operating system and applications are really upset with some people because they do not have the time, or sometimes the improvements in the new software version makes them feel familiar. For that reason, many of you will choose to turn off the auto-update, ignore the new updates and leave like that. However, when doing so is that you have inadvertently caused his computer to be "fragile" than with regular updates. Not when the manufacturer does not release the software update, it is used to fix the existing errors, improve software performance, add new features, interface changes ... With the operating system and increasing the error correction performance as more important because it helps us to work more smoothly, faster, less error prone than machines. It's wasteful when we refuse to use the improvements that developers hand delivered to us.
Therefore, take the time to try and update the software offline. With
Windows , you can set the machine to inform the new update and choose yourself the download / update, so it will be little slower, less Internet bandwidth occupied over. If you are able to install and update, the computer itself was wonderful then. Similar to other software applications, if you choose option than the temporary bypass. Most of the app will have a button "Remind me later" to remind you to update later, but remember it is not okay to ignore. Browser, Flash, Java needs to be updated regularly by the very things they are vulnerable to attack from outside.
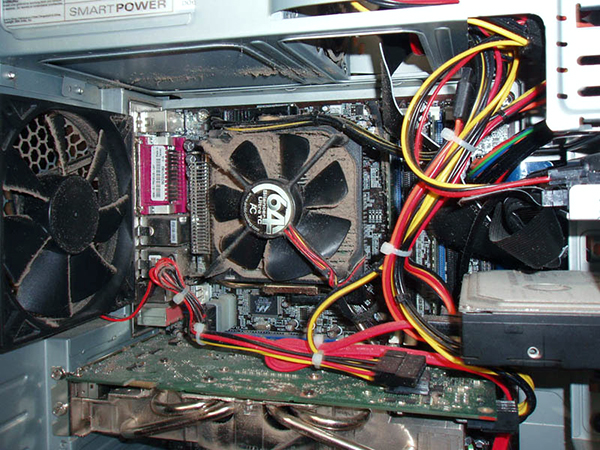
2. To close the computer too much dust
After a period of use, desktop or laptop will be dust. Dust will cause the fan turns slowly away, the air circulation is reduced and the temperature increase in our PC. If there is too much dust, heat dissipation system of the device may not work as good as the original design to computer overheating and the computer will automatically shut down. I once had a friend who uses a laptop, a system crash every 5 minutes even though he had installed the machine, complete software update, replace both batteries at. It turned out that due to the dense dust in the equipment slot radiator overheating and causing computer operating system of the PC-break operation. Just use the map blowing spray blowing dust a few times this condition is gone. Due rubber squeeze as they cost tens of thousands of contract and you can purchase at most computer stores.
To limit the above situation, you should always open the desktop case and cleaning inside it. In Vietnam, we do not have a lot of dust and gas should this need to be conducted more frequently. If you have time, you can do 2 a week, otherwise once a month. As for the laptop, you will need to open the machine for cleaning. It is very easy to open, with most laptops, we just need to open some screws underneath the machine, remove the bottom plate of the saw with the mainboard slot heatsink and fan. However, the laptop is able to stamp the warranty will be torn open, so if you are not familiar with it should bring out the best services to their computer to help you.
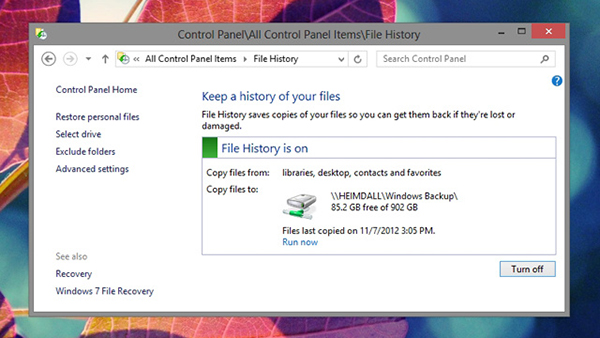
3. No data backup
I know this is very very very many people do, because they hesitate to take time, take extra backup capacity (!?). Even you know more about your computer and your data is not backed up by ... lazy. Why are you lazy while currently there are many tools for automated data backup? Just a little search on the Internet and you will see a lot of software has the function of "auto backup", both for Mac, Windows and Linux. Windows 8 users are even available free backup feature built into the operating system, you can also use the Mac Time Machine with equivalent functionality.Many data backup only proceed once they have experienced loss and "traumatic experience", do not become one of them okay for you.
A few rules when backing up data:
- Restrictions on the backup storage device installed in the computer: for example, many of you often create a backup partition on the computer and then copy data from drive C, drive D through it. This is almost useless because if you lose your computer, why? Or the hard drive fails, what to do? It is best to backup an external hard drive. HDD then current price is quite reasonable, just about 1 million is genuine 500GB drive to back up data before, about 700-800 thousand is good 320GB drive. If available HDD / SSD left over from the previous round of upgrade, please take advantage of it always okay. In addition, you also need to choose a safe place to put this backup drive offline. For example, if you put in pairs when theft is going to take the data on your computer and backup drive.
- Regular backups : backup set schedule at least once a week, not for a month to do this once because of no backup data is very large, consuming our time. In addition, the regular backup will also help to limit to the minimum amount of lost data in the worst case.
- Backing up on many different drives : if your data on the type of the utmost importance, the nature of "survival" with work or your life, do not regret the money again to buy a backup drive with a content. So you will have at least two backup drives, plus data on another computer, the safety is much higher. Of course, if necessary, feel alone, you do not need to invest in a backup drive Monday.
4. Plug the computer directly into a power outlet

You have the power cord plugged straight desktop or laptop into a power outlet is not? You should not do that okay by unstable power source, which can increase fire component, which power your home or flashes of lightning will be "poignant" this. Adapter laptop too, although not directly affect the computer, but the money to replace and fix adapter pretty much. Instead, you should plug in a splitter and from splitter plugged into the wall. The reason for the split will often fuse, if power is too strong, the fuse off, bought out electric shop instead is done, both cheap and fast. Some have not only broken, it fuses itself only, not the device is plugged in to the same fate, and then buy back the share is still cheaper than buying the adapter and computer components. You note that the Department should avoid sharing three (in some places called Trident) okay because we do not have fuses, protective effect is not there. Used to split the socket is pure.
5. Defragment SSDs
With HDD on computers running Windows, the defragmentation is commonplace and we have done this a long time ago. But with SSDs, so you should not defrag. Why?
HDD will write data to the disc plates, and top with the task of finding them when you need access to. It so happens that the HDD is a condition that one data file (probably) have been stored in the different parts of the blade disc, leading to the access speed is reduced significantly, referred to as the fragmentation (fragment). Therefore, the operating system will have a function called Defragment (Defragment) to collect the pieces of data together to reduce this situation.
However, SSDs are made as well as other mechanisms HDD activity. Data is stored on the Flash memory chip, so despite being fragmented, but SSD does not use the word to search for data access should still take place immediately. Therefore, do not need and should absolutely not run defrag app for your SSD. Doing this meaningless and even harmful to the SSD because it's starting to make an overworked (SSD longevity is calculated according to the number of write / erase data that defrag programs that move data from place to another).
6. Running multiple antivirus software at the same time
You should run only one antivirus program on your computer at a time only. The antivirus app will dig into the system to manage the operation of the machine, check the software before running, scan everything you download or peripherals are plugged into the PC. If you have more than one anti-virus app, they will conflict with each other during the operation makes the machine "behavior" strange, is even reboot or blue screen of death. Some even get anti-virus software as malware and try to remove it from your computer again.
Also because of this, usually, when the anti-virus software installed, you will receive a warning similar to what I said above. Some apps, such as Kaspersky or Norton, will not let you proceed with installation if not uninstall antivirus software are.
7. Blocking airflow heatsink
As mentioned whimper, the computer needs to be properly heatsink to work best. In addition to ensuring that dust does not stick in the slot with heatsink, make sure that you do not let anything stop before this gap. If you use a desktop, do not leave it against the wall thermal losses (or grab something covered) by the hot air has no place to escape. If using a laptop, do not let up mattresses gaming machines and other heavy work done by the mattress will block vents.Similarly, do not put your laptop in your lap if your thigh is capable of blocking the gas. Keep in mind that space for heat dissipation is critical, while surfing the web or simple chit chat is fine, but when running intensive tasks, the machine needs a lot cooler.
8. Using powerful graphics card overkill
If only the office if you need to AMD HD 7990 card for gaming?
Everyone likes to have a powerful PC, but most people do not use all the power of the machine. If you build a desktop for a girlfriend, the wife, the parents, the more likely you will not need a powerful graphics card, even using onboard graphics chip has enough. The powerful graphics cards will consume a lot of energy even when you are not running graphics-heavy tasks. That power waste our money to buy something that costs almost never need to. Even if you have enough money, you should not do that, please save to buy something else better, more useful.
9. Refrain from using old CRT
If you are still using the old CRT, it will consume a lot of power and thereby increase your electric bill. Not to mention the CRT has lightning phenomena (flickr) was not good for the eyes and cause headaches when used in a long time. If possible, upgrade to LCD or LCD screen with LED backlighting for the screen type current was also very cheap then, to have various sizes from small to large are spoiled for choice. In addition, the LCD screen also helps you save a lot of desk space compared to the old CRT monitors used, which are bulky and big.
10. Do not make the desktop and hard drive clean and tidy
Good practice is to always clean your desktop and hard drive to make it tidier and less cluttered than. It not only helps us to more easily find that sometimes your desktop neat and less on the things that will make your computer run faster - in case you use a Mac. For the hard drive too, the file is no longer used to delete it and gather them into a file folder to help management easier.Take time for other things instead of sitting for a picture file on your hard drive or a cluttered desktop.
Supplement:
11. Remove the laptop battery when plugged in
This was a mistake that countless people have. You could argue that removing the battery and power only helps for longer battery life than the bottle, when you replace the battery on time.However, this is dead wrong because if the voltage is not stable or components may burn, and least flammable source chip. I've met a lot of you are like that then, very traumatic experience.With Macs, had proven that the test remove the battery and only power plant efficiency will decrease significantly.
The battery of the laptop is now using a new technology, besides it will interrupt power to the battery when the battery to 100% and switching to new sources should be used very long cylinders only a few% only. You should not worry then, lo the damaged machine back to the suffering. You want to change the batteries last few years a million times or want to spend money to fix my laptop?